Network Security Policy and Traffic Detection on a Network
What are Intrusion Detection Systems?
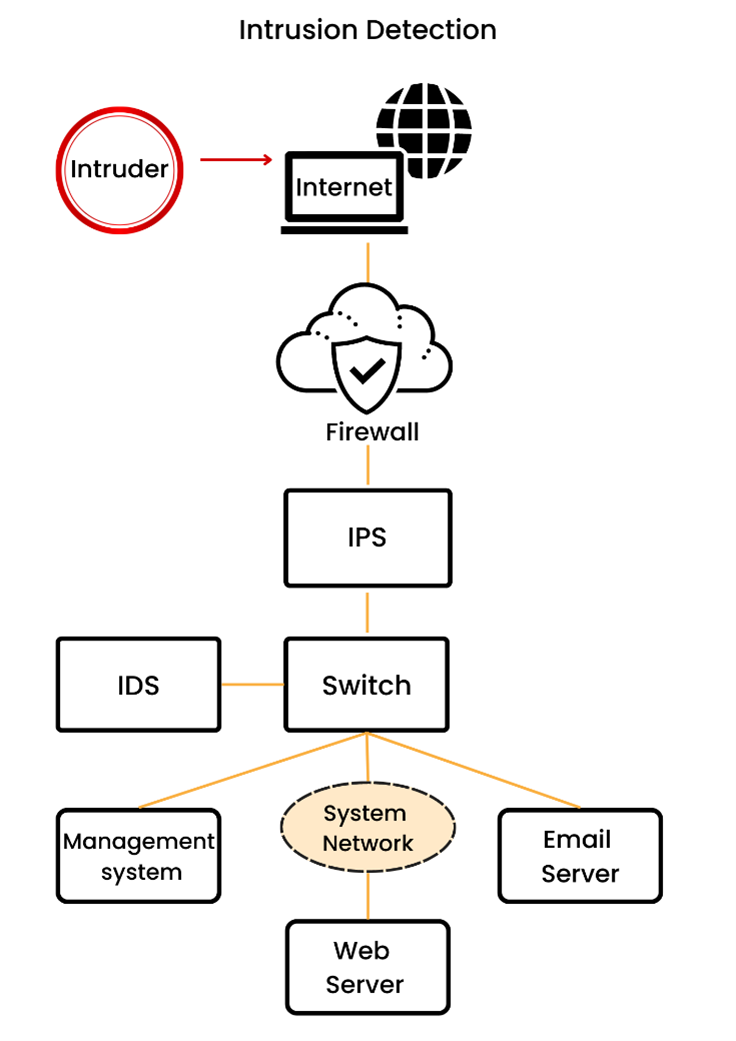
Intrusion detection or Intrusion detection systems (IDS) commonly work within a network to monitor its traffic for malicious content and breaches of policy. It differs from an Intrusive Prevention System (IPS) as an IPS works to remove a threat while IDS works to monitor and alert of a prospective malicious intent that can be investigated without acting on the problem itself.
IDS can be applied strategically within a network at notable choke points where data flows, such as a checkpoint where data must go before moving on to a new destination layer or transfer through some interface. If the point may produce some sort of breach or becomes hacked or can be a problem within an intrusion scenario, then the IDS can alert the correct function to combat the threat or fix any issues. It can identify potential bugs in a network and IDS can work to spot false negatives within a network, which can be patched to better coordinate for a large-scale attack and prepare accordingly. IDS usually acts as the last line of defense in the transfer of data from one location to another.
Architecture with Potential Intrusion and Placement within a Network (Source: Lumenci)
IDS can be applied on both a small-scale network and a large one but work in tandem with IPS to provide security on multiple parts of a network. Network Intrusion Detection Systems (NIDs) and Host-based Intrusion Detection Systems (HIDS) are some types of IDS that work within some of the more present prevention issues of a system. NIDs are applications that passively monitor traffic on the network while HIDs work to dynamically monitor all activity on a system to be aware of malicious intent.
Abnormal traffic of any kind can diverge from regular traffic – even a small margin can cause the network to be checked by an IDS – and these systems work out differences from regular traffic. NIDS work within two interfaces – one to regulate control and reporting of network traffic and promiscuous mode. Promiscuous mode takes the flow of data and corrals it into one location to be viewed, regardless of the destination address or network. Then the data can be sniffed for any variance of data flow – analyzed and registered according to software rules defined on a network. Sniffing may happen once or multiple times as information from data packets can cross network traffic in varying instances. HIDs work similarly to log data, but they track what applications are used, file access points, and store information from a host end-to-end perspective.
Methods for Networks and Firewalls
As a part of intrusion detection, many detection methods may be employed to detect attack signatures on a network. Anomaly-based detection methods work within the scope of newer malware. Two sets of generative data may be developed that compare to each other to check behaviors within a projected network or test an environment. If something from the testing has not been seen before that could be intrusive, the label can be added to a database as a threat. Signature-based methods work based on traffic signatures, like the regulated flow in the HIDs defined above. Detected patterns are defined as a signature and added to a record to prevent future attacks of a similar pattern.
IPS systems also contain their detection methods. Stateful protocol analysis detection as an IPS measures events on a network versus pre-configured parameters. There is a set amount of safety levels, and a threat may be included in a threshold value that can be checked. Signature-based detections of IPS work to track packets of a network that have already been seen before working through an attack pattern– such as packet flow behaving abnormally. Lastly, statically anomaly-based detection works within the regular traffic flow variances, and this proceeds to check the network. If values do not associate correctly based on configurations on a network, a false positive may ensue.
An additional integral part of a network system following an IDP and IPS comes from a firewall. As the IDP monitors network flow, the IPS will detect and block traffic intrusions labeled as a threat, wherein the firewall works in tandem with the two to block and allow traffic at the forefront of the network with the IDP and IPS behind it. Firewalls come in several forms - Unified Threat Management (UTM) firewalls and Next-Generation Firewalls (NGFW) stand out among them. UTM services utilize several protection plans on a single network. Content filtering, anti-spam measures, and antivirus are some of the actions provided by a UTM. NGFWs provide the same services above, but they work to reduce the level of redundancy within those developed features – filtering can be turned on in case of trusted certificates on a website, for instance, or fewer levels of content need to be filtered as traffic through a website or network has been verified previously.
Patent Publication Trends (Source: Lumenci)
In the specialty of intrusion systems, the industry has seen significant growth over the last five years, with record numbers of patents being published. Filings are still accelerating, with patent publications doubling in 2020-2021 from the previous year. As security measures continue to develop and network intrusions evolve, developments will have to keep up with the continued upkeep of the security of systems and networks.
Conclusion
The combination of monitoring, detection, and prevention systems in networks will continue to tackle challenges with adverse attacks on systems finding unique ways to bypass network systems. As networks rely on detection systems as one standard of security measure against outside threats of malware attack, intrusion, or threat, developments must continue for security to combat intrusions to network systems and attacks.
Author
SangJin Hyun
Associate Consultant at Lumenci
SangJin is an associate consultant at Lumenci with experience in mobile applications and software development. His work at Lumenci focuses on source code review and product testing of various mobile devices and software technologies. He holds a bachelor of science in computer science and is a computer science graduate of the University of Illinois at Urbana Champaign.