Access Control Mechanisms
Access Control is a way of granting or denying access to a set of information or resources. The exponential increase in data generation and maintenance has also brought unique challenges and requirements for stringent privacy protection and security. Advances in networking and cloud computing have increased collaboration between multiple users. As a result, this also makes networks and systems vulnerable to the threat of attacks and data leaks. Data access to unwanted entities can cause data security issues, monetary losses, and raises impending privacy concerns for the organizations. Imposing access control has become a crucial part of data and information security for these reasons.
Why Access Control is important and useful:
Enables User Identification, Authentication, and Authorization
Access Control requires user identification and authentication to ensure it belongs to the permitted set of users to request access. Access Control grants or limits user access to resources.
Distinguishes real users from bots
Access Control can assess user access patterns to identify malicious bots and deny access to help protect data privacy. Bots are often used to mimic human behavior and can perform automated and sometimes harmful, tasks.
Detects malicious activity
Anomalous user access behavior often indicates suspicious network activity. Access Control can aid in the timely detection of security threats and prevent them.
Aids in Intrusion Detection
Access Control helps detect anomalous user activity and helps safeguard systems from intrusion and security breaches.
Provides selective access to help maintain confidentiality
Restricting users that should not be accessing the information and resources keeps data confidential, protected, and less prone to leakage.
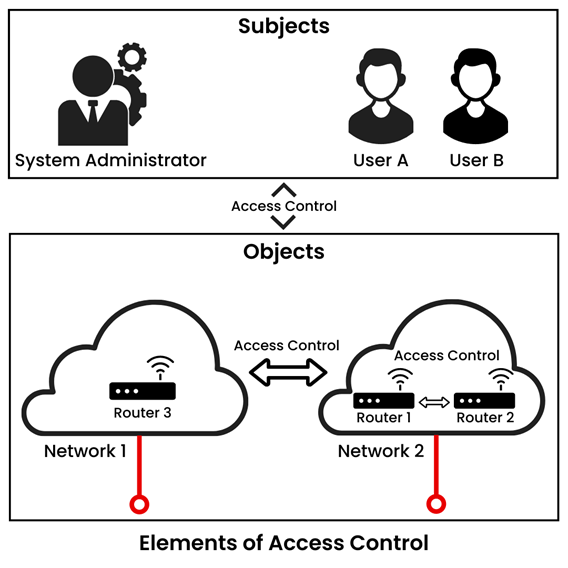
Elements of Access Control
Access Control is commonly formulated for two conceptual entities: Subjects and Objects.
Elements of Access Control (Source: Lumenci)
Access Control Policy and Models
Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. International Organization for Standardization (ISO) defines security standards that organizations must comply with to ensure and execute data privacy and security. Access Control Lists implement these policies for a system or network resource component.
Access Control Models provide a defined structure to implement access control policies. Organizations can choose to implement one or a combination of the access control models based on the custom security requirements and existing infrastructure.
The following are some of the common types of access control models:
Discretionary Access Control (DAC): The data owner decides the users’ selection and the permissions to be granted to users that access the data.
Access control of this type is simple to implement and maintain. Users get more autonomy over the changes if they have access rights.
Such approaches might run into conflicting user permissions and might not be as secure as other approaches.
Mandatory Access Control (MAC): Organization’s administrator sets strict policies on individual users and/or the data, resources, and information accessed by the users. Users cannot add, alter, or remove any permissions.
Such models can be used when central access policies are enforced, and it is easier to compartmentalize resource access to a subset of users.
However, this model might not be a requirement for an organization that depends highly on collaboration and lacks management resources to implement the model.
Role-Based Access Control (RBAC): The system administrator decides the level of priority or access given to users based on their role in the organization. The assigned permissions allow the user limited access to resources or limited permissions to information. The users can perform actions or access information based on the level of visibility granted by the RBAC.
This approach is very flexible and makes it easy to maintain user access for well-defined organizational hierarchies.
The role and responsibility assigned to the users can pose a risk to overprivileged users due to the complexity of the access assignment.
Attribute-based Access Control (ABAC): This is a context-based dynamic policy. The access control is based on policies assigned to the users.
Being attribute-based and dynamic, this approach is more targeted, robust, and scalable.
The implementation process is quite complicated and time-consuming.
Break-glass Access Control: Generally implemented in case of emergency, a user generally not authorized is given access or allowed to create a new account which would not be permitted in normal conditions.
This approach can help prevent threats or mitigate damages in case of a security emergency.
Generally, this is used in emergencies and is not too secure or meant to be used for long-term needs.
Rule-based Access Control: System Admin defines certain condition-based rules limiting company resource access.
Spatial Access Control: Access control conditions are location-based.
Temporal Access Control: Access control conditions are based on the time of day the access is requested.
This approach serves great for custom and specific access requirements. It provides more granular control and flexible options for access setup.
To ensure reliable security, this approach demands extremely diligent designing of rules.
Temporal Access Control
Time-based access control/temporal access control is a way of determining whether to grant or deny access to a user based on the time of the day that the access was requested. It plays a crucial role in the authorization of user access. It is used to control access to inbound or outbound traffic access or control. Temporal access control can be for a defined time range (absolute or periodic) or a custom time frame.
Absolute: Define a particular date and time or time range when access is granted or prohibited to a set of certain users.
Periodic: Define access control for a certain time range that repeats after a certain period.
Firewall settings can define the temporal access control of a network and network devices for a user or set of users. Permissions can be set and altered accordingly.
Based on Figure 1 above, the following are some scenarios/examples of time-based access control;
Selective User Access to Selective Network Devices:
On December 3, 2022, 1-3 AM, User A has access to change the settings of Router 1 but at the same time, User B has no permissions.
Selective User Access to the entire network:
On Tuesday 4-6 AM, no user has access to any network devices in the network.
Selective User Access:
For Saturday and Sunday, 10 AM- 6 PM, User B has permission to alter settings for Router 2, but User B cannot shut down the system.
When the system is down for maintenance, only the system admin will have access to set and alter permissions for users.
Selective Network Device Access:
Router 1 cannot ping Router 2 every Thursday between 2-5 PM.
Router 3 can ping Router 2 only on Nov 22, 2022, between 5-10 PM; otherwise, all requests are directed towards Router 1.
Detecting anomalous network activity:
Temporal access control can help detect anomalous user activity and prevent malicious attacks by blocking access based on access control.
Using Machine Learning and Network Analytics, it is possible to detect anomalous, malicious, or suspicious network activity and can help prevent threats like intrusion, DDOS attacks, data leakage, etc.
For example, the usual login activity of User A is Monday- Friday, 8 AM – 9 PM.
Set alert, add user authentication/verification, or block login access for all login requests made from User A’s account outside general login hours.
Patents
In the past decade, there has been extensive research in the cybersecurity space to build more innovative and robust systems. Different types of approaches are being tested to combat challenging security concerns. Following are examples of network security patents that use access control and anomaly detection to design effective cybersecurity solutions.
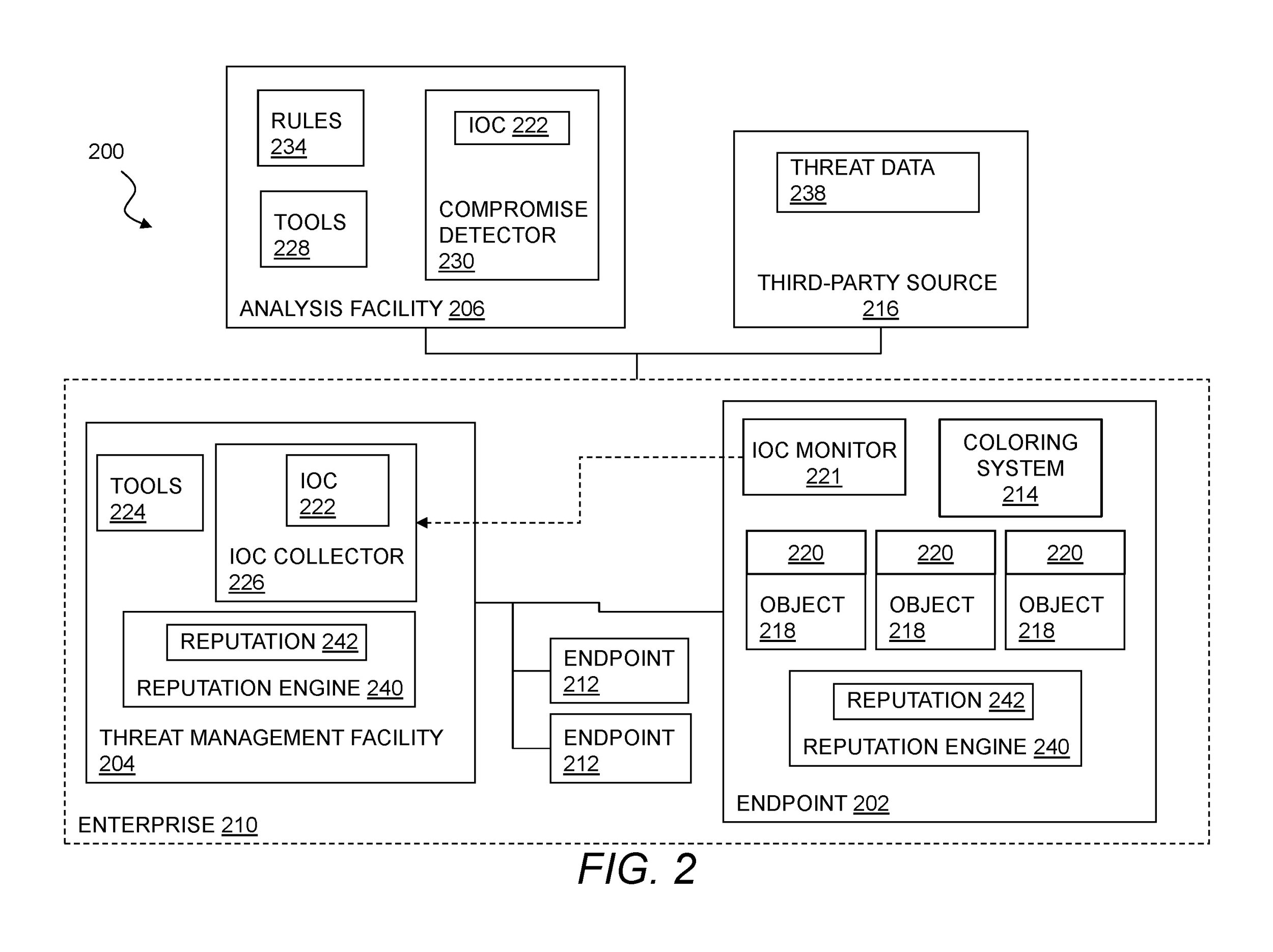
Sophos Ltd holds a patent US10382459: ‘Threat detection using a time-based cache of reputation information on an enterprise endpoint’. This system and method describe a way of threat detection at the network endpoint using reputation scores for action with a finite time expiry. In case of a networking event at the endpoint, the system assigns context-based labels to the action like the data category, static threat detection attributes, and identification markers. Based on the complex interaction between these labels, and similar cached data, the system assigns a reputation score to flag whether the action should be considered a threat. The threat management facility then takes remedial action. Threat detection at the endpoint reduces communication overhead and helps secure the network to avert further damage.
With the rise of different cloud computing platforms and the increase in user collaboration, ensuring network security is fundamental, and static access control may not suffice the requirements. Microsoft owns a patent - US10454934: ‘Activity-based access control in heterogeneous environments’. This patent provides a system, method, and infrastructure to implement user activity-based dynamic access control in heterogeneous environments. By analyzing user activity related to cloud service access and usage, the heterogenous authorization system dynamically grants or revokes user access to a set of services. This helps secure data from the risk of theft, tampering, hijacking, accident, or unwanted content alterations.
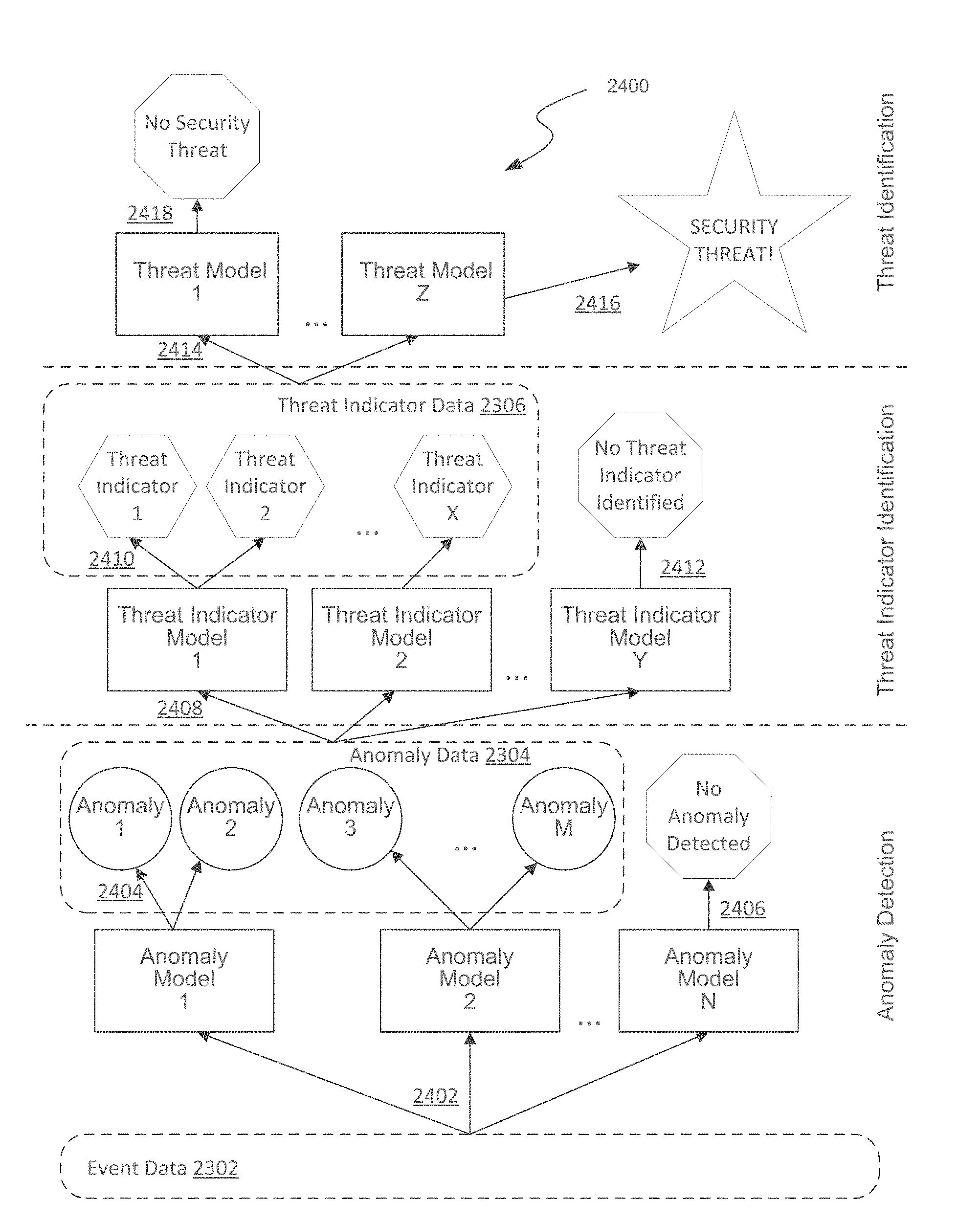
Palantir Technologies, a well-known industry leader in big data analytics, owns a networking patent in this space- US11310254: ‘Network anomaly detection’. It describes a system and method to use advanced network analytics to detect anomalous user behavior. It considers a combination of data parameters like user activity logs, origins of user activity, hostname, username, IP address, and timestamp of user logins, etc. The system then compares this data to find other similar users, sorts them into a cohort, and compares new user activity to the cohort activity to determine anomaly. This system provides a dynamic, more accurate approach to network security while reducing manual intervention in the process.
Real-time threat detection on streaming data is quite challenging. Splunk’s patent US9900332: ‘Network security system with real-time and batch paths’ addresses this concern. It describes a method and system/platform to help network administrators detect threats in distributed data systems in real-time. It uses Apache Spark Streaming based computation engine to detect the first indicia of a security threat in the network. Using machine learning algorithms, it generates and stores real-time analysis of this activity, which is then used in batch mode to detect the second possible security breach event in the network. This approach uses user/entity behavior analytics to detect security anomalies- known or unknown. It operates both in real-time and batch modes. Visual presentation of analytics results based on risk rating and evidence aid network administrators in taking network security decisions.
Conclusion
With the increase in data growth and access, cyber security has faced unique challenges to protect organizational and personal data from malicious attacks and vulnerabilities. This paves the way for innovative combative solutions. CyberArk’s Privileged Access Mechanism provides a solution to combat hacking by detecting and preventing misuse of privileged access control of an organization. AWS, a popular cloud computing platform by Amazon, authenticates and authorizes users by employing IAM (Identity and Access Management) to provide robust and secure access to resources. Other popular cyber security companies like CISCO, Fortinet, CrowdStrike, FireEye, DarkTrace, etc., have started combining access control with AI, Machine Learning, and network analytics to build intelligent cybersecurity solutions. Be it to distinguish real users from malicious bots or to prevent network intrusion by detecting anomalous user behavior, access control proves to be a crucial contributor to data privacy and protection.
Author
Maitreyee Mhasakar
Associate Consultant at Lumenci
Maitreyee has been a consultant to multiple law firms for Infringement Analysis, Product Testing, Source Code Review, Technical Document Review, and public domain technology research. She has signed PO in the WACO division for multiple cases. The technologies she covered previously are related to streaming services and Codec technology. She has also worked on ideation related to IP Strategy for a startup. Maitreyee is a Master of Science in Computer Science from the University of Texas at Dallas.