Quantum Cryptography – The Future of Secure Communication
Introduction
Quantum technologies are among the most exciting and rapidly developing emergent technologies of the 21st century. It is expected that numerous commercial applications would emerge from the theoretical constructs developing globally in this field. Quantum technology seeks to harness laws of quantum physics, which describe the behavior of matter and energy at the atomic and subatomic levels.
This is unlike classical physics, in which an object can exist in one place at one time. E.g., classical computers operate using binary physical states, meaning their operations are based on one of two positions (1 or 0). Quantum principles will be used for engineering solutions to extremely complex problems in computing, communications, sensing, chemistry, cryptography, imaging, and mechanics.
Some applications of Quantum Technology are:
Quantum Computing has potential applications in precise navigation for defense and civilian applications, accelerated drug development by accurate chemical simulations, etc.
Quantum metrology provides a more capable means of detecting stealth aircraft and submarines, mineral exploration, water resource management, etc.
Quantum Communication
Quantum communication applies the laws of quantum mechanics to data protection. It uses quantum bits (Qubits), typical photons of light, for transmitting data along optical cables.
The following are the most common technologies of quantum communication, which are in different stages of development:
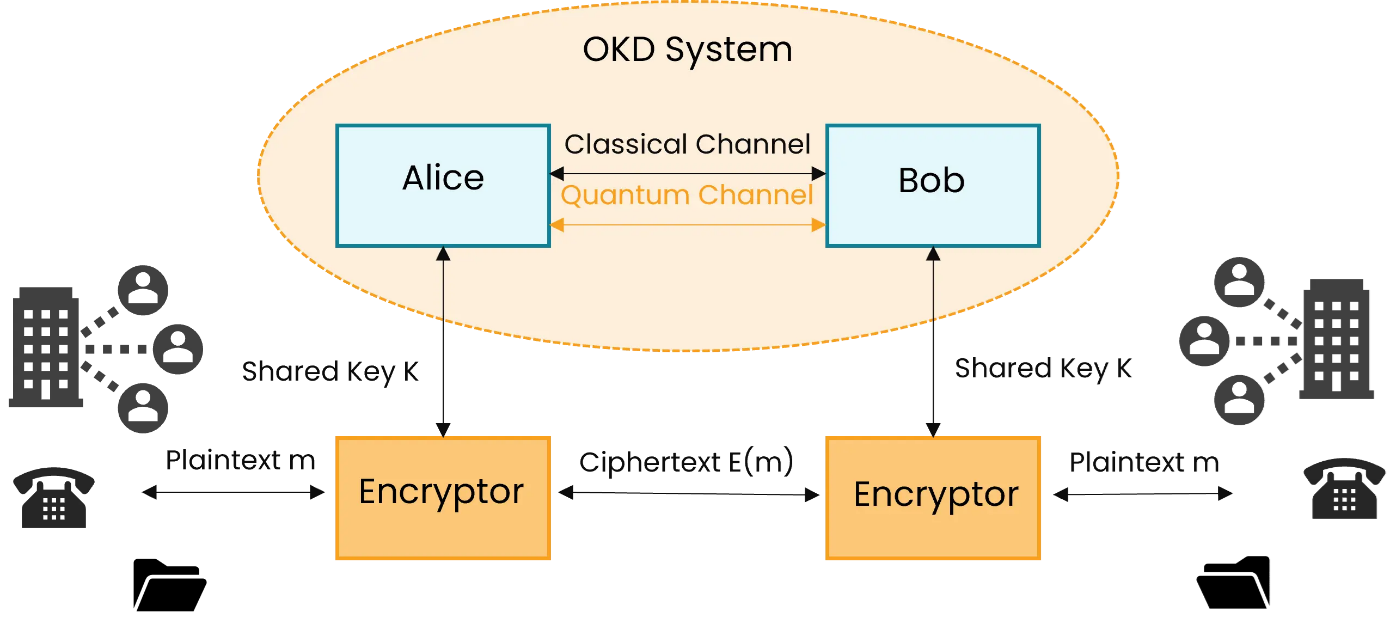
Quantum Key Distribution: QKD is a secure communications technology that enables two parties to share random secret keys known only to them and can be used to encrypt or decrypt messages.
It involves sending encrypted data as classical bits over networks while the keys to decrypt the information are encoded and transmitted in a quantum state using qubits.
A remarkable feature of QKD is that it can detect if a third party tries to eavesdrop on a communication link.
QKD system is encrypted and detects third party interference (Source: Lumenci)
Quantum Random Number Generation (QRNG): Random numbers are mainly used as seeds in cryptosystems (cryptographic algorithms needed to implement a particular security service such as encryption) to generate keys. The strength of these keys depends on the randomness of the input.
QRNG detects random quantum events and converts those into a stream of binary digits. Quantum mechanics has the inherent potential of providing true random numbers and thus has become the preferred option for scientific applications requiring randomness.
About Quantum Key Distribution (QKD):
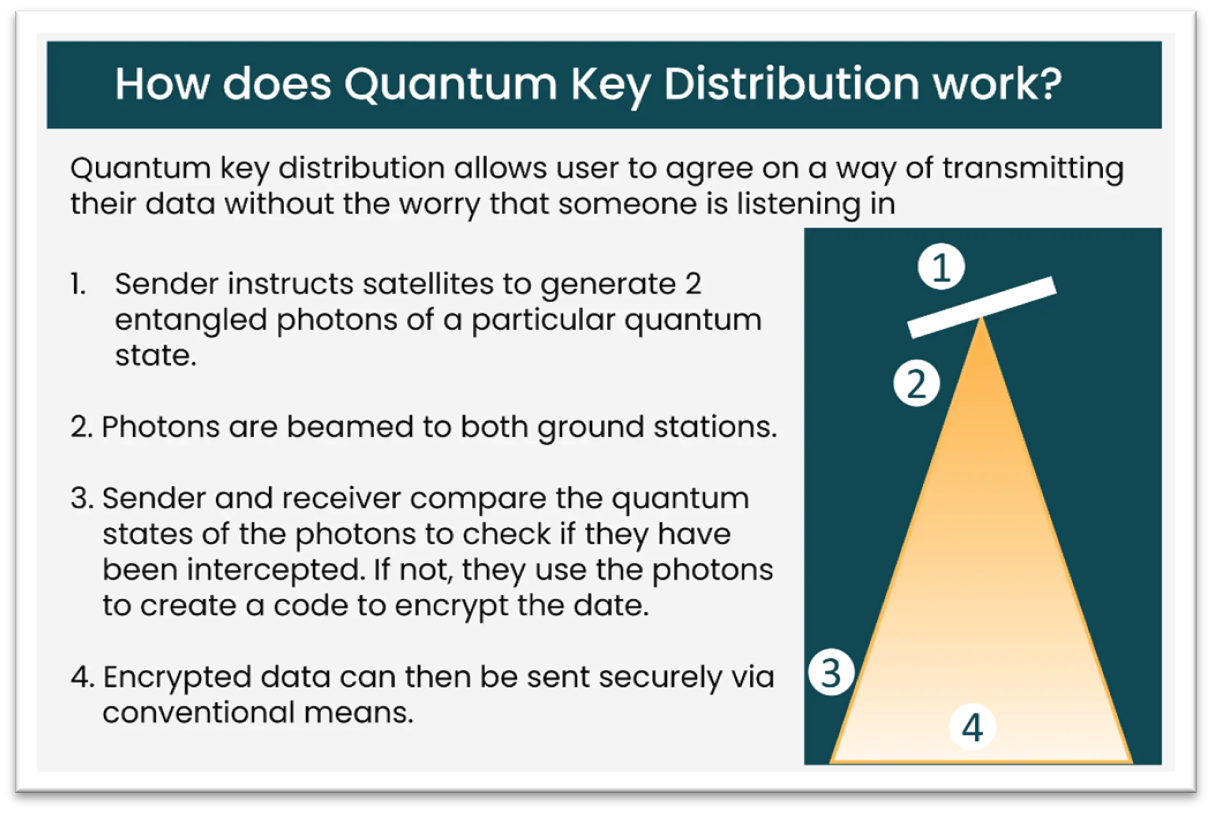
QKD is a secure communication technology that uses quantum physics to construct a cryptographic protocol. It allows two parties to generate a shared secret key that is only known to them and can be used to encrypt and decrypt messages, thus achieving highly secure communication.
In traditional cryptography, security is usually based on the fact that an adversary cannot solve a certain mathematical problem while in QKD, security is achieved through the laws of quantum physics.
Two such most important laws in quantum physics are Superposition and Entanglement.
a) Superposition means that each quantum bit (basic unit of information in a quantum computer) can represent both a 1 and a 0 simultaneously.
b) In quantum entanglement, subatomic particles become “entangled” (linked) in such a way that any change in one disturbs the other even if both are at opposite ends of the universe.
Two main categories of QKD are prepare-and-measure protocols and entanglement-based protocols.
Prepare-and-measure protocols focus on measuring unknown quantum states. This type of protocol can be used to detect eavesdropping, as well as how much data was potentially intercepted.
Entanglement-based protocols focus on quantum states in which two objects are linked, forming a combined quantum state. In this method, if an eavesdropper accesses a previously trusted node and changes something, the parties involved will know.
Challenges Associated with QKD
A central challenge in implementing QKD over long distances and at high communications rates is the ‘transmission loss’ in optical fibers.
Communication rate is another parameter where QKD falls short compared to classical communications.
Current classical optical communications deliver speeds on the order of 100Gbit/s, whereas QKD communications achieve rates in the range of Mbit/s (100,000 times less).
Integration of QKD Systems into Current Infrastructure:
For now, it is currently difficult to implement an ideal infrastructure for QKD.
QKD is perfectly secure in theory, but in practice, imperfections in tools like single photon detectors create many security vulnerabilities.
Distance in which photons can travel:
Modern fiber optic cables are typically limited in how far they can carry a photon. Commonly, this range is seen to be upward of 100 km.
Advantages of QKD
It will enable security agencies to plan a suitable quantum communication network with indigenous technology backbone.
Quantum cryptography is considered ‘future-proof’ since no future advancements in computational power are known to break a quantum cryptosystem.
Secure communications are vital not just for defense and strategic agencies across the globe but also for various civilian applications.
The Patent Landscape
With the continuous development of science and technology, especially the quantum computer, cyberspace security has become the most critical problem for the Internet in the near future. Data transfers using quantum cryptography are much more secure than those that use traditional cryptography because quantum methods rely on the laws of physics instead of the impracticality of calculating certain mathematical problems. The issue of safeguarding these unique ideas is a serious consideration for companies pushing the boundaries. No innovator wants their creations stolen or misused. This is where intellectual property comes in.
Large organizations spend a lot of time, money, and effort in Research and Development to ensure their innovations are patented. This gives them an edge in the market as their technology is secure and cannot be copied elsewhere. Some of the big players that have focused their patent activities on Quantum Cryptography technology are listed below.
Top 10 conglomerates in Quantum Cryptography patent landscape (Source: Lumenci)
With the biggest number of active grants, Google, the world’s biggest conglomerate, sits comfortably at the top. MagiQ Technologies is an organization that announced the availability of a commercial quantum key distribution product (Navajo) back in 2003. The list of strong competitors also includes other names, such as Japan’s NEC Corporation, which invests heavily in the quantum cryptography field.
If we observe the top countries/jurisdictions where quantum cryptography patents have been filed. In this United States of America tops the list, followed by Europe. As quantum cryptography is a very modern and advanced technology, huge R&D investments are required, and such demands can be mainly catered to in economically and technologically advanced countries.
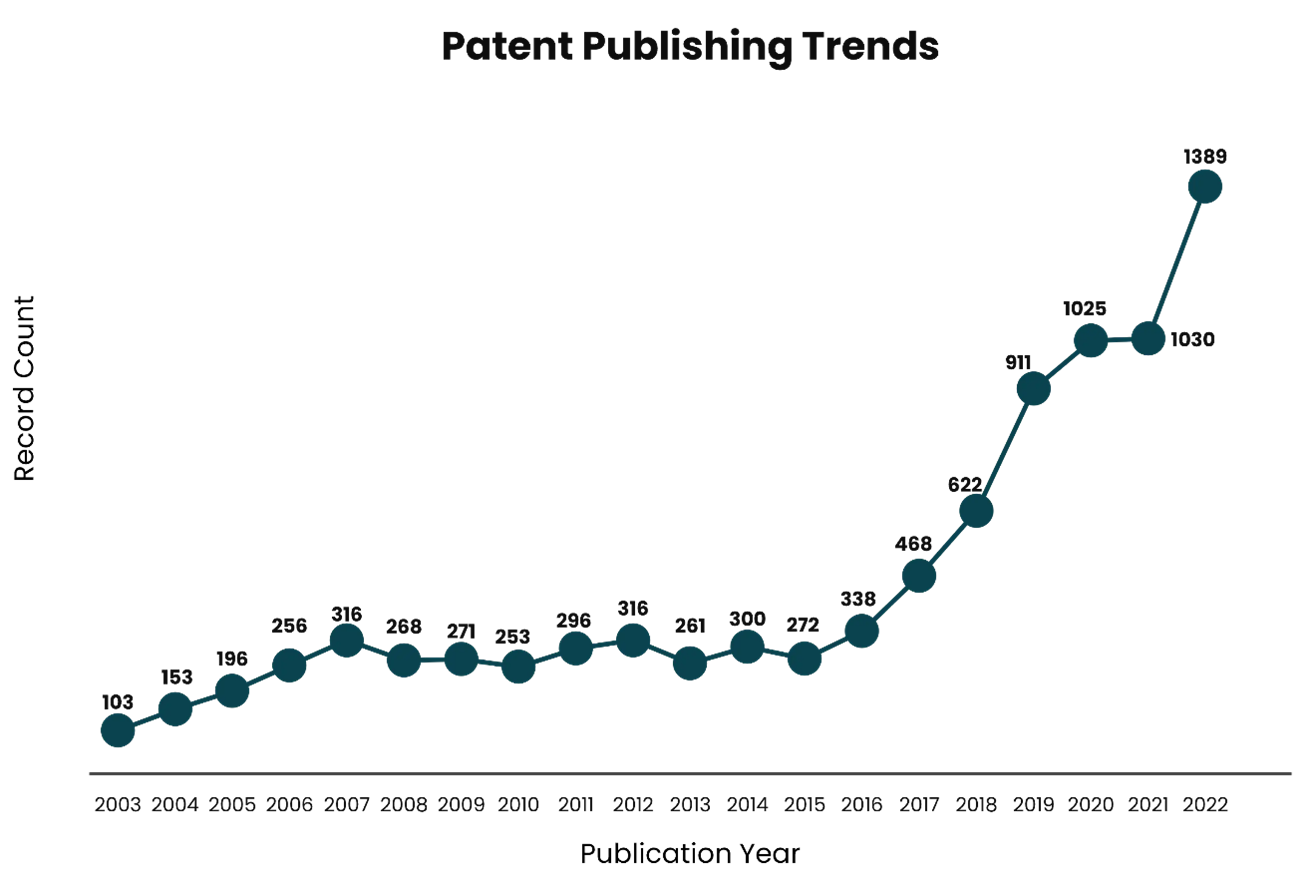
If we observe the patent publishing trends in this domain for the past twenty years, we can see a steep rise after 2015. This rise can be mainly credited to the increased focus on data security as more sophisticated data/work/operations are happening on the internet leading to more data vulnerability. Quantum Cryptography provides much more secure systems and information transfers than traditional cryptographic algorithms because quantum methods rely on the laws of physics for securing systems/information etc.
Conclusion
As a revolutionary technology, Quantum Cryptography may ensure exceptional communication security. Its unique principles can facilitate message transmission that is secure against tampering. Yet, in the early stages of development, quantum cryptography has great potential for the future of secure communication. It can become a widely adopted technology in the future with growing cases of data breaches and cyberattacks.
Author
Somesh Singh
Associate Consultant at Lumenci
Somesh has experience in working with growing technologies in the fields of cryptography, security, and blockchain, where the technology ranges from Encryption Algorithms, and Quantum Key Distribution. He also has expertise in technologies related to Augmented Reality, Virtual Reality and Mixed Reality among others. He is a Computer Science engineer from UPTU with an LLB from Delhi University and a PGD from NLSIU Bangalore, India.